Moving Apps to Azure Part 2: Create Azure Resources for Your ASP.Net Application
This blog series provides a step-by-step guide to download a simple ASP.Net application and move it to an Azure PaaS environment. This is intended to...
7 min read
 Mick Sternick
:
Dec 16, 2020 10:15:00 AM
Mick Sternick
:
Dec 16, 2020 10:15:00 AM


If you are looking for the biggest buzz word in the world of Information Technology it is security, and rightfully so. With the dispersion of computing devices, work from home, and the move to the cloud, security has taken on a new role in the modern workplace. If you took a trip in the way back machine (like 5 years ago 😊) security was more network based. This made sense at the time since workplace users were all logging into a network to share information; if only authorized users were in the network, there was not much to worry about. Today that is ancient history.
Industry best practice dictates to institute a Zero Trust policy. This policy falls under 3 main tenets:
Verify explicitly: Rather than trust users or devices implicitly, the assumption is the request is from an uncontrolled network. Now we verify and track user identity, location, service, data classification and anomalies.
Least-privileged access: Cloud services provide fine grained control, this allows users to be granted just enough access to complete their job.
Assume a breach: Now we just assume we will be attacked. Rather then be reactive we are proactive. Use real-time analytics and policies to both defend and soften the impact of a security breach.
With this new world comes a mountain of technological advances behind it. Azure Security is a vast subject and can be daunting to both seasoned IT professionals, who are now asked to implement it, as well as new engineers looking to expand their knowledge base. We all want rock solid security, but the question is where to begin?

One of the easiest ways to begin implementing Azure Security is Identity Protection. Start off by logging in to portal.azure.com. From there, go to Azure Active Directory -> Security -> Identity Protection. Identity Protection is part of Azure Premium P2 license. Microsoft allows you a one-time 30-day trial so you can test out Identity Protection. You will be prompted on this screen for the trial if you do not already have Azure P2. After activating the trial, you will receive 100 licenses. Wait for an email and go to the license page and apply one to your account. After applying a license when you navigate back to Identity Protection you will see the trends and tiles on your page.
Click on ‘Get a Premium trial to use this feature. ->’ to open the Activate blade.
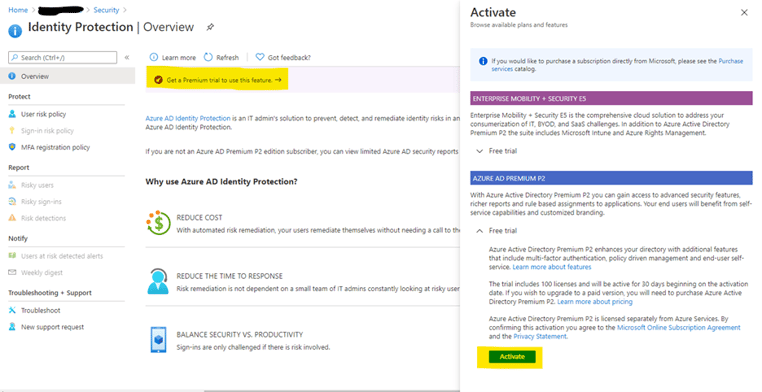
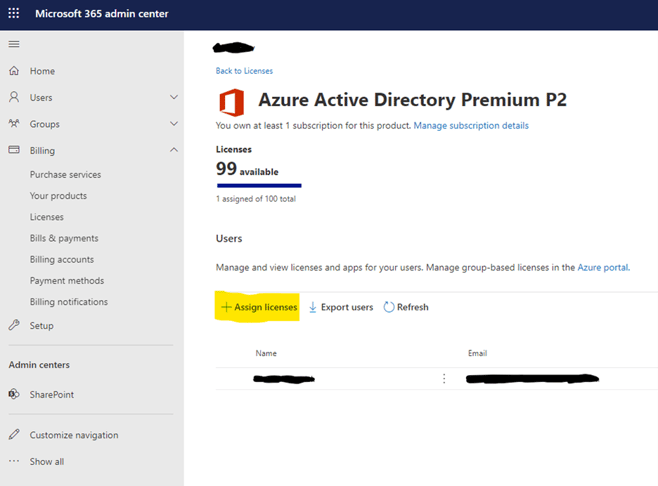
Your email will include a link to the Microsoft 365 Admin Center -> Licenses -> Azure Active Directory Premium P2 page. Assign a license to yourself to start using Identity Protection. You can also navigate there by going to admin.microsoft.com -> Billing -> Licenses -> Azure Active Directory Premium P2.
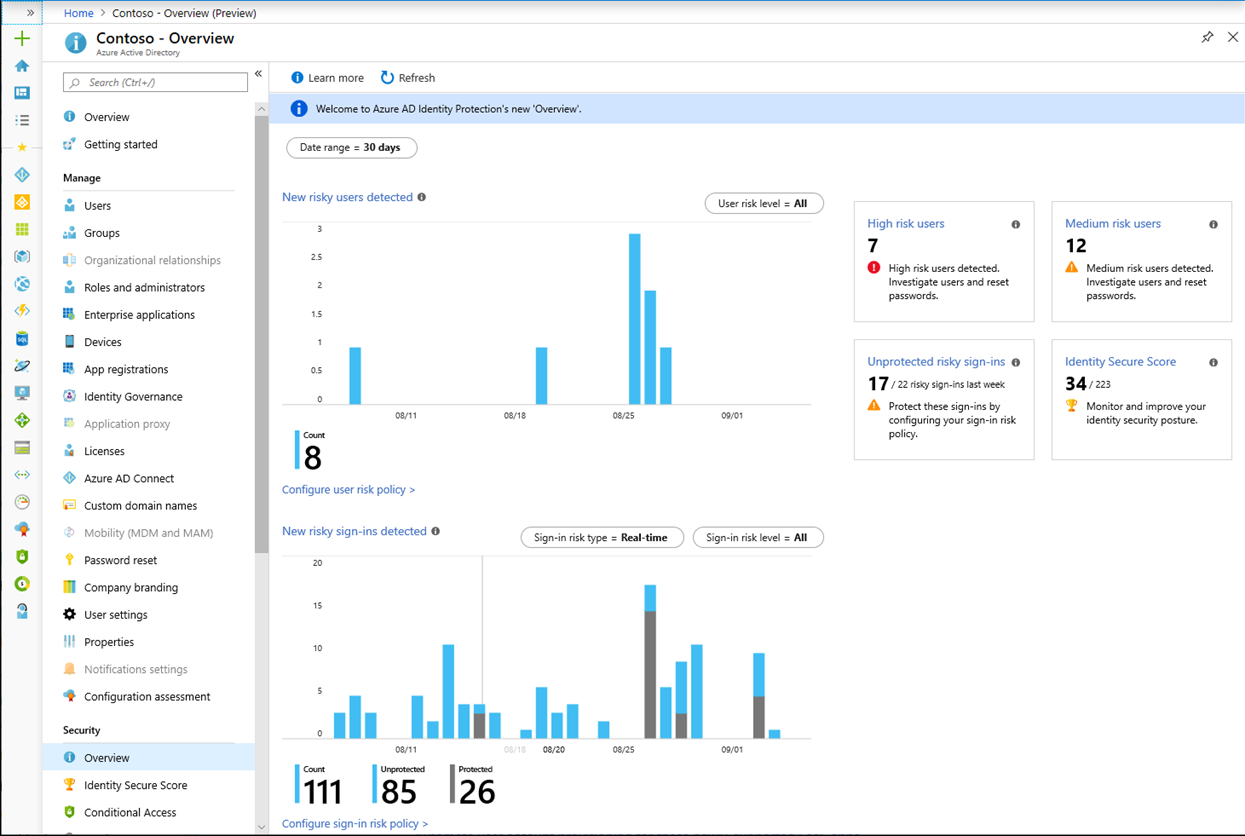
Now, when you navigate to the Identity Protection page you will see the trends and tiles.
Risk detections in Azure AD Identity Protection include any identified suspicious actions related to user accounts in the directory. Risk is broken into two types: User and Sign-In. The calculation that is done to detect risk has two types: Real-time and Offline. Real-time detections show up in 5-10 minutes while Offline detections show up in 2-24 hours.
A user risk represents the probability that a given identity is compromised. These are calculated using Microsoft’s internal and external thread intelligence sources including security researchers, law enforcement professionals and security teams at Microsoft.
|
Risk detection |
Description |
|
Leaked credentials |
This risk detection type indicates that the user's valid credentials have been leaked. When cybercriminals compromise valid passwords of legitimate users, they often share those credentials. This sharing is typically done by posting publicly on the dark web, paste sites, or by trading and selling the credentials on the black market. When the Microsoft leaked credentials service acquires user credentials from the dark web, paste sites, or other sources, they are checked against Azure AD users' current valid credentials to find valid matches. |
|
Azure AD threat intelligence |
This risk detection type indicates user activity that is unusual for the given user or is consistent with known attack patterns based on Microsoft's internal and external threat intelligence sources. |
A sign-in risk represents the probability that a given authentication request isn't authorized by the identity owner.
|
Risk detection |
Detection type |
Description |
|
Anonymous IP address |
Real-time |
This risk detection type indicates sign-ins from an anonymous IP address (for example, Tor browser or anonymous VPN). These IP addresses are typically used by actors who want to hide their login telemetry (IP address, location, device, etc.) for potentially malicious intent. |
|
Atypical travel |
Offline |
This risk detection type identifies two sign-ins originating from geographically distant locations, where at least one of the locations may also be atypical for the user, given past behavior. Among several other factors, this machine learning algorithm takes into account the time between the two sign-ins and the time it would have taken for the user to travel from the first location to the second, indicating that a different user is using the same credentials. |
|
Malware linked IP address |
Offline |
This risk detection type indicates sign-ins from IP addresses infected with malware that is known to actively communicate with a bot server. This detection is determined by correlating IP addresses of the user's device against IP addresses that were in contact with a bot server while the bot server was active. |
|
Unfamiliar sign-in properties |
Real-time |
This risk detection type considers past sign-in history (IP, Latitude / Longitude and ASN) to look for anomalous sign-ins. The system stores information about previous locations used by a user, and considers these "familiar" locations. The risk detection is triggered when the sign-in occurs from a location that's not already in the list of familiar locations. Newly created users will be in "learning mode" for a period of time in which unfamiliar sign-in properties risk detections will be turned off while our algorithms learn the user's behavior. The learning mode duration is dynamic and depends on how much time it takes the algorithm to gather enough information about the user's sign-in patterns. The minimum duration is five days. A user can go back into learning mode after a long period of inactivity. The system also ignores sign-ins from familiar devices, and locations that are geographically close to a familiar location. |
|
Admin confirmed user compromised |
Offline |
This detection indicates an admin has selected 'Confirm user compromised' in the Risky users UI or using risky Users API. To see which admin has confirmed this user compromised, check the user's risk history (via UI or API). |
|
Malicious IP address |
Offline |
This detection indicates sign-in from a malicious IP address. An IP address is considered malicious based on high failure rates because of invalid credentials received from the IP address or other IP reputation sources. |
|
Suspicious inbox manipulation rules |
Offline |
This detection is discovered by Microsoft Cloud App Security (MCAS). This detection profiles your environment and triggers alerts when suspicious rules that delete or move messages or folders are set on a user's inbox. This detection may indicate that the user's account is compromised, that messages are being intentionally hidden, and that the mailbox is being used to distribute spam or malware in your organization. |
|
Password spray |
Offline |
A password spray attack is where multiple usernames are attacked using common passwords in a unified brute force manner to gain unauthorized access. This risk detection is triggered when a password spray attack has been performed. |
|
Impossible travel |
Offline |
This detection is discovered by Microsoft Cloud App Security (MCAS). This detection identifies two user activities (is a single or multiple sessions) originating from geographically distant locations within a time period shorter than the time it would have taken the user to travel from the first location to the second, indicating that a different user is using the same credentials. |
Let us examine each one of the trends, policies, and tiles located in Identity Protection to see what they provide for us.
This chart shows the number of risky users that were detected over a chosen period of time (UTC). Filter by user risk level (low, medium, high) which is configurable in Configure user risk policy (see below). Clicking on this chart will show you the risky users report.
With the information provided by the risky users report, administrators can find:
Administrators can then choose to take action on these events. Administrators can choose to:
This takes you to the configuration blade for the User risk remediation policy. Here you can configure:
This chart shows the number of risky sign-ins detected over the chosen period of time (UTC). Filter by risk type (real-time or aggregate) and sign-in risk (low, medium, high). Clicking on this chart will take you to the risky sign-ins report.
The risky sign-ins report contains filterable data for up to the past 30 days (1 month).
With the information provided by the risky sign-ins report, administrators can find:
Administrators can then choose to take action on these events. Administrators can choose to:
This takes you to the configuration blade for the User risk remediation policy. Here you can configure:
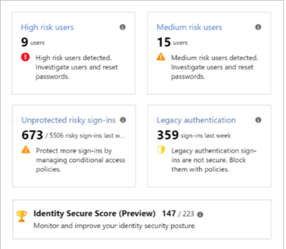
This tile shows the latest count of users most likely to have their identity compromised. Clicking on this tile will take you to the Risky users report where you can investigate further and force a password reset.
This tile shows the latest count of medium probability users with identity compromise. This report also takes you to the Risky Users report with risk level filtered to medium risk.
This tile shows the last week’s count of successful, real-time risky sign-ins that were not blocked or MFA challenged by a Conditional Access policy, Identity Protection risk policy, or per-user MFA. These are potentially compromised logins that were successful and not MFA challenged. You should apply a sign-in risk policy by clicking on this tile to take you to the sign-in risk policy configuration blade.
This tile shows the last week’s count of legacy authentications with risk present in your organization. Legacy authentication protocols do not support modern security methods such as an MFA. To prevent legacy authentication, you can apply a Conditional Access policy. Clicking on this tile will redirect you to the Identity Secure Score blade.
The Identity Secure Score measures and compares your security posture to industry patterns. Clicking on this takes you to the Identity Secure Store blade. This score falls between 1 and 233 that functions as an indicator for how aligned you are with Microsoft’s best practice recommendations for security. Each improvement shown is tailored for your organization, implementing them will increase your score.
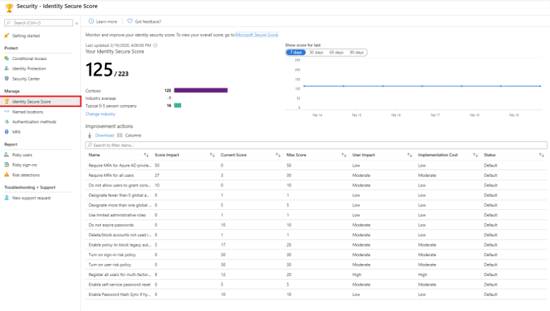
Every 48 hours Azure compares your settings with recommended best practices and evaluates a new score for you. If your security configuration isn’t fully aligned, then you will receive a partial score.
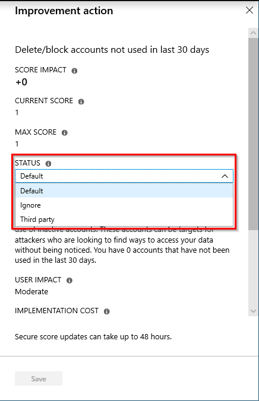
The secure score helps you to:
Do you still have questions or are you interested in learning more? Contact us today!

This blog series provides a step-by-step guide to download a simple ASP.Net application and move it to an Azure PaaS environment. This is intended to...

Preparing the security and compliance needed to safely and securely leverage Copilot Copilot is one of the next big things from Microsoft and will be...
.png)
Copilot as a suite of solutions from Microsoft continues to roll out for almost every solution that Microsoft currently publishes. The current suite...